
Tech Risks: Why Backdoor Attacks are a Growing Concern for Disabled Users
Cyberattacks are increasing all the time and disabled people can be vulnerable to backdoor attacks. They often rely on assistive technologies and attackers can exploit weak points in the technology. A backdoor attack can have serious repercussions for disabled people.
What are backdoor attacks?
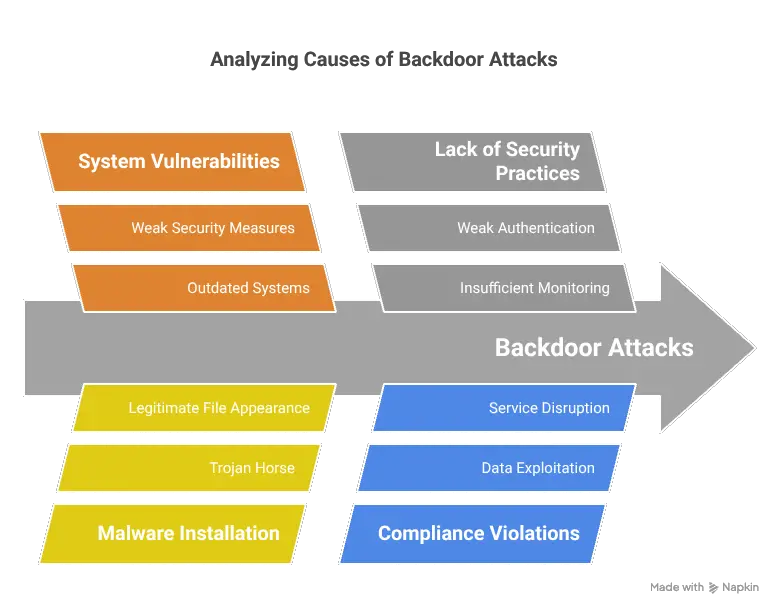
In a backdoor attack, the attacker uses a weak point to bypass standard security measures and gain unauthorised access to a system, application, or network. An attacker can also use malware, such as a Trojan, to install a backdoor. The system grants it access because it looks like a legitimate file. Once it’s installed, the attacker has a way in and can cause significant damage.
One backdoor attack example from 2017 that many people remember is the WannaCry attack on the NHS. Attackers used the outdated Windows systems to gain a backdoor. This had a significant impact on healthcare services. It particularly affected disabled people needing regular monitoring and care. A backdoor attack can lead to the exploitation of sensitive data and resources. This may include personal data, intellectual property, and financial records. It can disrupt services, cause downtime and result in fines or lawsuits for compliance violations.
Organisations can suffer reputational damage and financial harm from a backdoor attack. For backdoor cybersecurity, they need to know how to prevent backdoor attacks. They can use third-party software to scan for malware and remove it. Other measures are to use strong security practices and automatically update operating systems and installed applications.
Why are disabled people especially at risk?
Disabled people may rely heavily on assistive technology. This technology may be vulnerable to backdoor attacks. Assistive devices can range from simple ones like hearing aids to complex hardware and software. This technology enables them to participate in daily life and work.
Mobility devices include wheelchairs, some of which are Bluetooth-enabled. Vision aids include screen readers and Braille displays. Communication aids may include speech-to-text software. Smart Home Devices can help to automate tasks and offer more independence.
Real-world examples
Android’s Accessibility Service
Android’s Accessibility Service helps disabled people with visual or motor impairments. This includes screen readers, a text-to-speech function, and automated touch interactions. In 2018, malicious apps were found abusing accessibility permissions. They were performing unauthorised actions such as reading screen content. They also granted themselves elevated permissions (a soft backdoor). People using the service were at higher risk as they had to enable these permissions for usability. This opened a larger attack surface.
Braille devices
This wasn’t publicised much because no mass attack occurred. In 2016, the Lazarus Group, a North Korean hacking group, reportedly scanned and tested Braille devices for entry points. Security researchers found backdoors and outdated operating systems on devices like a leading digital notetaker.
How to protect yourself
Various measures can help you to prevent backdoor attacks.
Use strong authentication
Create complex passwords that contain uppercase and lowercase letters, numbers, and symbols. Don’t use the same one for all your devices. Two-factor authentication can add another layer of security. It requires a second verification method, such as a code sent to your smartphone for access.
Keep operating system and software up-to-date
Security patches and updates address weak points hackers can exploit to install backdoors. Enabling automatic updates is wise. Removing or disabling non-essential software can reduce potential entry points for attackers.
Ensure network security
Any unusual activity on a network could indicate the use of a backdoor. Make sure to activate the firewall as it provides a barrier that can block unauthorised access to a network and devices.
Consider using a Virtual Private Network (VPN). This is particularly important when using public Wi-Fi. It encrypts internet traffic which makes it harder for attackers to intercept data.
Use trusted tools
- Reputable antivirus software can detect and remove backdoor malware or a backdoor virus.
- Only download software from trusted sources and scan files for malware before running them.
- Create regular backups of your important data and store it securely in case of a breach and data loss.
What should tech companies do?
Tech companies need to call for inclusive cybersecurity measures and more transparency. They need to ensure that users know about safe app practices and regular updates. Running an attack surface security assessment is one way providers can uncover vulnerabilities in assistive technology and strengthen protections for disabled users.
Advocacy is important to ensure that disability-related technology isn’t just an afterthought. Users should feel that they can reach out to the tech company that made the assistive technology for guidance and support.
Conclusion
Disabled people who rely heavily on assistive technologies can be vulnerable to backdoor attacks. They may feel backdoor attacks are a not a relevant technical issue but it can cause huge disruption. Taking various protective measures can reduce this risk.
Resources
AbilityNet has a helpline that offers disabled people or those who support them advice from technology experts.
The National Cyber Security Centre (NCSC) makes practical guidance on cyber security available to all.
The Business Disability Forum offers resources, such as a document on assistive technology and IT security. It helps organisations manage risks associated with assistive technology in the workplace.
FAQs
What does backdoor mean and how does it relate to accessibility tech?
A backdoor in cyber security is when attackers exploit a weakness to gain access to a system or network without the knowledge of a user. Accessibility tools such as voice control systems often require elevated permissions to function properly. This can make them attractive targets for attackers.
Why are disabled users particularly vulnerable to backdoor attacks?
Disabled people often rely on assistive technologies that may run on outdated or unsupported operating systems. This makes them vulnerable to backdoor attacks.
What can disabled people do to protect against backdoor attacks
Measures they can take to protect themselves against backdoor attacks include using strong authentication measures and keeping their operating systems and software up to date. They should consider using a Virtual Private Network (VPN) to encrypt internet traffic and use trusted tools like antivirus software.
Author Bio:
Gabriel Jones is an online marketing professional with expertise in content writing, search engine optimisation and link building. From travel to health and technology to gadgets, he covers various niches to help local businesses, SMBs and startups gain traffic organically and ensure higher conversion rates.